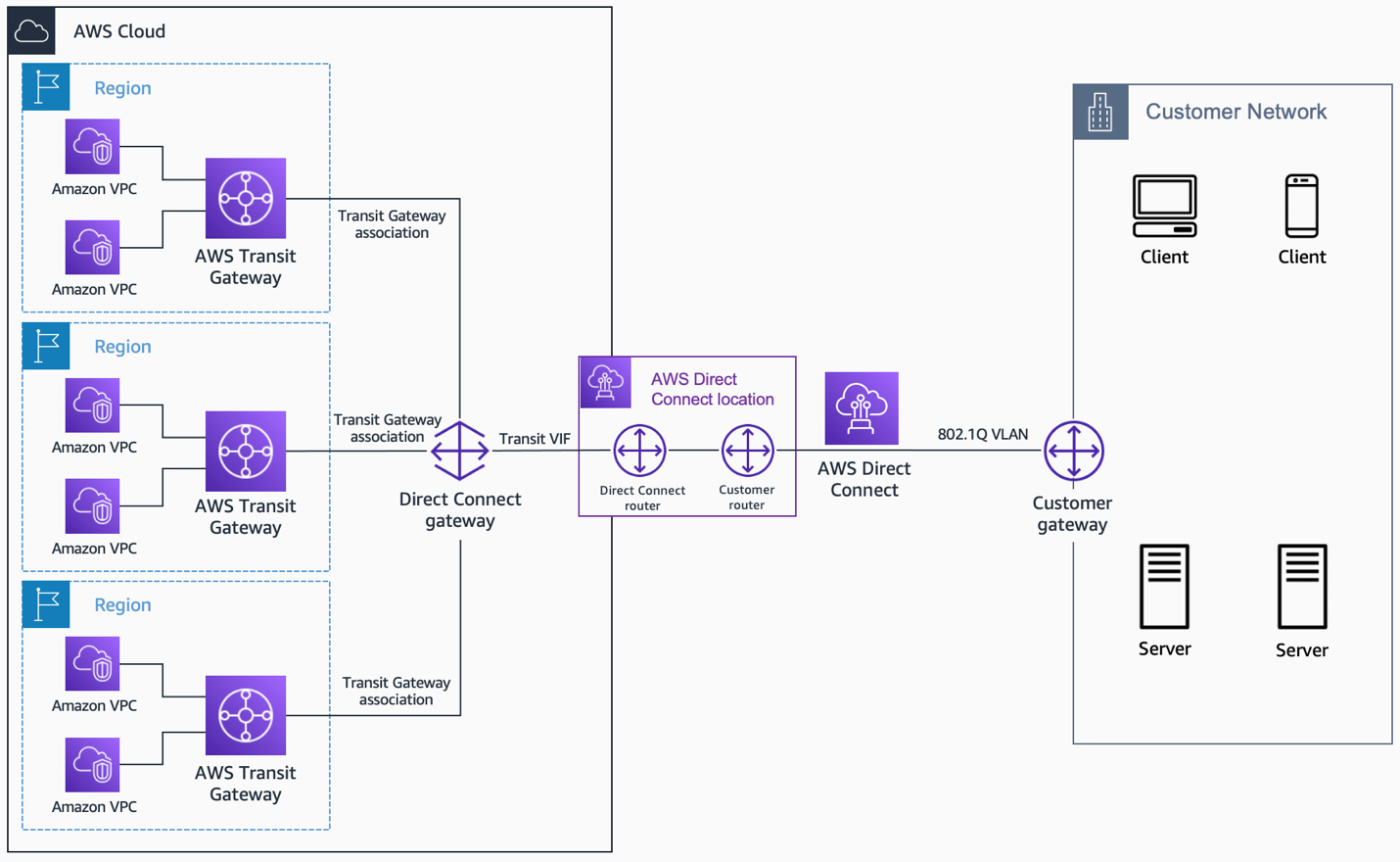
Connecting remote IoT devices securely to AWS VPC is essential for maintaining robust cybersecurity in modern cloud infrastructures. As the Internet of Things (IoT) continues to grow exponentially, ensuring secure communication between devices and cloud environments has become a top priority for businesses. In this article, we will explore strategies, best practices, and step-by-step processes to securely connect remote IoT devices to AWS Virtual Private Cloud (VPC).
The rise of IoT has transformed industries by enabling smart devices to communicate seamlessly over the internet. However, this interconnectedness also introduces security risks, making it crucial to implement robust security measures. By leveraging AWS VPC, organizations can create a secure and isolated network environment for their IoT devices, protecting sensitive data and maintaining operational integrity.
This article aims to provide a detailed guide for IT professionals, developers, and decision-makers who want to enhance their understanding of secure IoT connectivity within AWS VPC. We will cover essential concepts, tools, and configurations to ensure your IoT ecosystem remains protected against potential threats.
Read also:Onlyfans Leaks Understanding The Phenomenon And Protecting Yourself
Table of Contents
3. Why Choose AWS VPC for IoT?
4. Bi-Directional Secure Communication
5. Best Practices for Secure IoT VPC
6. Network Security Techniques
Read also:Maplestar The Ultimate Guide To Understanding Its Impact And Significance
6.1. Firewalls and Access Control
7.1. IoT Device Authentication
8. Data Protection and Privacy
8.1. Data Encryption in Transit
9. Tools and Services for Secure IoT VPC
10. Future Trends in IoT Security
1. Introduction to AWS VPC
AWS Virtual Private Cloud (VPC) is a service that allows users to launch AWS resources into a virtual network. This virtual network closely resembles a traditional data center, enabling organizations to have complete control over network configurations. By using AWS VPC, businesses can define subnets, IP address ranges, route tables, and network gateways, creating a secure and isolated environment for their IoT devices.
AWS VPC offers several features that are beneficial for IoT deployments, including:
- Customizable IP address ranges
- Multiple subnets for better organization
- Security groups and network access control lists (NACLs)
- Integration with other AWS services
These features make AWS VPC an ideal choice for securely connecting remote IoT devices to the cloud.
2. IoT Security Challenges
The proliferation of IoT devices has introduced several security challenges that need to be addressed. Some of the most common challenges include:
- Limited computational resources on IoT devices, making encryption and security protocols difficult to implement.
- Unsecured communication channels that expose devices to potential attacks.
- Device misconfigurations that can lead to vulnerabilities.
- Insufficient authentication mechanisms, making it easy for unauthorized access.
Addressing these challenges requires a comprehensive security strategy that includes both hardware and software solutions.
3. Why Choose AWS VPC for IoT?
AWS VPC provides several advantages for IoT deployments, including:
- Isolation: AWS VPC allows you to create a private and isolated network environment for your IoT devices, reducing the risk of unauthorized access.
- Scalability: AWS VPC can scale to accommodate the growing number of IoT devices, ensuring your infrastructure remains flexible and adaptable.
- Integration: AWS VPC seamlessly integrates with other AWS services, such as AWS IoT Core and AWS Lambda, enabling advanced functionalities like data processing and analytics.
By leveraging AWS VPC, organizations can build a secure and scalable foundation for their IoT ecosystems.
4. Bi-Directional Secure Communication
Ensuring secure communication between IoT devices and AWS VPC is critical for maintaining data integrity. Bi-directional secure communication involves securing both inbound and outbound traffic to prevent unauthorized access and data breaches.
Key strategies for achieving bi-directional secure communication include:
- Implementing secure communication protocols like MQTT over TLS.
- Using AWS IoT Core for device authentication and message routing.
- Configuring security groups and NACLs to control traffic flow.
These strategies help ensure that data transmitted between IoT devices and AWS VPC remains secure and protected.
5. Best Practices for Secure IoT VPC
To securely connect remote IoT devices to AWS VPC, it is essential to follow best practices. Some of these practices include:
- Regularly updating firmware and software to patch vulnerabilities.
- Using strong authentication mechanisms, such as X.509 certificates, for device identification.
- Monitoring network traffic for suspicious activities using AWS CloudWatch and AWS Shield.
By adhering to these best practices, organizations can significantly enhance the security of their IoT deployments.
6. Network Security Techniques
6.1. Firewalls and Access Control
Firewalls and access control lists (NACLs) are essential components of network security. They help filter traffic and restrict access to specific resources within the AWS VPC. By configuring firewalls and NACLs correctly, organizations can prevent unauthorized access to their IoT devices.
6.2. Encryption Protocols
Encryption protocols play a vital role in securing data transmitted between IoT devices and AWS VPC. Protocols like TLS and SSL ensure that data remains confidential and tamper-proof during transmission. Organizations should use the latest encryption standards to protect sensitive information.
7. Remote Device Management
7.1. IoT Device Authentication
Device authentication is critical for ensuring that only authorized devices can connect to the AWS VPC. AWS IoT Core provides robust authentication mechanisms, such as X.509 certificates and AWS IoT Device Defender, to secure device access.
7.2. Secure Firmware Updates
Regular firmware updates are necessary to patch vulnerabilities and improve device functionality. Organizations should implement secure firmware update mechanisms to ensure that updates are delivered safely and efficiently.
8. Data Protection and Privacy
8.1. Data Encryption in Transit
Data encryption in transit ensures that data remains secure while being transmitted between IoT devices and AWS VPC. Using protocols like TLS and SSL, organizations can protect sensitive information from interception and tampering.
8.2. Data Encryption at Rest
Data encryption at rest protects stored data from unauthorized access. AWS provides several services, such as AWS KMS and Amazon S3, that enable organizations to encrypt data stored in their VPC.
9. Tools and Services for Secure IoT VPC
AWS offers a range of tools and services to help organizations securely connect IoT devices to their VPC. Some of these tools include:
- AWS IoT Core for device management and communication.
- AWS Lambda for serverless data processing.
- AWS CloudWatch for monitoring and logging.
By leveraging these tools, organizations can build a comprehensive security framework for their IoT deployments.
10. Future Trends in IoT Security
The future of IoT security is shaped by emerging technologies and evolving threats. Some of the key trends to watch include:
- Increased adoption of edge computing for processing data closer to the source.
- Advancements in artificial intelligence and machine learning for threat detection and response.
- Development of new encryption standards to address quantum computing threats.
Staying informed about these trends will help organizations prepare for the future of IoT security.
Conclusion
Securing remote IoT devices within AWS VPC is crucial for protecting sensitive data and maintaining operational integrity. By following the strategies and best practices outlined in this article, organizations can build a secure and scalable IoT ecosystem. We encourage readers to implement these solutions, monitor their networks regularly, and stay updated on the latest security trends.
We invite you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our website for more insights into cloud computing and IoT security.